Rich Nass, OpenSystems Media In the Internet of Things (IoT) era, everything is connected and each connection point can be viewed as a target by hackers. To prevent this, developers need verification and security version control to ensure that all firmware and related patches are up-to-date. Any unpatched or outdated firmware allows access to critical system features. Unfortunately, the development team often ignores the need to update the firmware after the product is shipped. In many cases, this is due to the resources required and the complexity involved. But what if the entire process of updating and protecting firmware via remote or wireless (OTA) is standardized and encapsulated in a reliable solution that works seamlessly with the underlying hardware and is easy to use? It turns out that such a solution already exists. Whether it's an error in an embedded system, a bug, or some other problem, the responsibility for the repair is usually borne by the software/firmware team. Repairing software is much easier and less expensive than fixing it in hardware. This is a logical reason. From a security perspective, eliminating vulnerabilities is usually the responsibility of software because almost every remote attack is implemented through weaknesses in software or firmware. Why is this? Because launching an attack via firmware (remotely or otherwise) is much simpler than launching an attack with hardware that requires an entity. If a device is connected to the Internet of Things, these firmware security vulnerabilities could affect millions of devices. Vulnerabilities in device firmware can also provide access to private information, corporate data, and even medical information. In addition, if a hacker gains access to the operating system (OS), they can completely take over the device and compromise the entire network. Assuming continuous discovery of new vulnerabilities, the challenge is to respond quickly to avoid any impact or minimize impact: the longer the vulnerabilities exist, the more likely they will be exploited and the more damage they will inflict. . By standardizing the update process, compatible operating systems can apply firmware updates to any platform, just as easily as operating system drivers or application updates. Because the IoT device is connected, it can seamlessly check and download updates wirelessly, and it is possible to close the vulnerability quickly on the same day that the hotfix is ​​released. This assumes that the developer has resolved some issues related to implementing OTA updates. With OTA updates, OEMs can now remotely close firmware vulnerabilities. However, there are two major challenges in implementing OTA updates safely and effectively. The first challenge is to distinguish outdated firmware components from current firmware components in a given system. Firmware updates usually require a reset of the device, which can be costly for some systems, so it is necessary to minimize the frequency of updates. To identify the components that need to be updated, it is important to remember that the firmware is not completely uniform. Many individual ICs and other components on IoT devices include their own firmware, so developers and security professionals must cross the BIOS to determine which of the various components can be updated. The second challenge is to determine if the new firmware version is verified and safe. To help designers quickly meet these challenges and make OTA firmware updates a more natural part of the product design and support cycle, OEMs are leveraging the updated encapsulation technology of the Unified Extensible Firmware Interface (UEFI) specification. This isolates specific firmware components for updates. When implemented in a commercial UEFI BIOS firmware solution, these solutions can monitor the updateable firmware component version and accept only "confirmation-free" firmware versions for updates. UEFI update packaging technology ensures that the entire system firmware remains as capable as possible Protect against attacks. Implementing the UEFI specification allows platform firmware to be extended by loading UEFI drivers and application images (Figure 1). After these images are loaded, the image has access to all UEFI-defined runtime and boot services. Figure 1. By loading the UEFI driver and application images defined by the UEFI specification, these images have access to all UEFI-defined runtime and boot services. (Source: Insyde Software) The UEFI firmware provides the EFI System Resource Table (ESRT), which describes all updatable firmware components and their versions on the IoT device. This allows the OS to detect a firmware update when a firmware update is available. Of course, if an update brings more problems than it solves, then such an update is not enough. For example, you would not want to upload a "new" version that is actually older than the existing version. And you definitely don’t want to upload a version that contains malware, or a version for an IoT device vendor. For this reason, the UEFI package (including its version) encrypts the signature through an authentication key embedded in the flash memory device. This allows UEFI encapsulation to be performed before UEFI firmware executes third-party code during the boot process. With this technology, IoT device manufacturers understand that their products are safe, so they can sit back and relax. OEMs can also minimize the time required to send patches, and the time saved can be used to develop revenue-generating services. However, for developers, to take full advantage of this technology, it would be helpful to have an off-the-shelf OTA version control and verification solution. Insyde Software has developed such a solution. Its InsydeH2O has been tested in hundreds of different platform types and can help IoT device developers quickly respond to firmware security vulnerabilities by supporting a simple update transport mechanism. It has been tested in hundreds of different platform types and can help IoT device developers quickly respond to firmware security vulnerabilities by supporting simple update transport mechanisms. The software then accepts the verified updates and applies them in a secure environment. As mentioned above, ESRT reports the current version of all updatable firmware components. The InsydeH20 firmware flash utility utility H2OFFT allows users to quickly and easily update flash devices with new BIOS firmware, even if the operating system or local IT administrator does not provide connection access to the firmware update. InsydeH20 can be implemented with OTA updates to ensure that the IoT device firmware remains secure and up-to-date. It can achieve this by locking the flash memory and letting the operating system know which firmware version is currently running. The operating system will then accept the verified firmware update. InsydeH2O then rechecks to ensure that the vendor authorizes the new version. The security update process does not provide more protection than the processor provides for flash devices that have firmware. Insyde Software takes advantage of the capabilities of the Intel Atom® C3000 processor to ensure the security of next-generation Internet of Things edge devices. The Intel Atom® C3000 processor allows InsydeH2O to lock the flash device and protect it from unauthorized changes later. In addition, Insyde BootGuard on the Denverton Innovation Engine can validate the first firmware bit before it is executed to support secure code authentication provided by the NIST-800-155 guide. By combining standards-based firmware update technology with hardware security features, OEMs can repair vulnerabilities in devices deployed in the field. Furthermore, technologies such as InsydeH20 can proactively monitor the firmware version to ensure that the firmware version is secure and up-to-date, freeing the developer from the need to manually check the status of each firmware component on the connected device throughout the life cycle of the firmware component. . Developers can now focus on creating value-added services, but more importantly, they can greatly reduce the possibility of hacked IoT systems becoming headlines.
We are professional audio manufacturing company that makes a variety of speaker with bluetooth, including bluetooth portable speaker, bluetooth speakers outdoor, small speaker bluetooth, light bluetooth speakers, waterproof speakers etc.
With full turnkey service from product design to delivery, and every step in between.
From sophisticated custom audio systems to 'off-the-shelf' speaker drivers, iTopnoo has been saving our customers time, effort, and money.
To constantly offer clients more innovative products and better services is our consistent pursuit.
Best Portable Speakers,customizable bluetooth speaker, Custom jbl speakers, speaker wholesalers TOPNOTCH INTERNATIONAL GROUP LIMITED , https://www.mic11.com
Software/firmware teams often face security risks
Update expired firmware: development dilemma
UEFI Update Package: Isolated, Secure Firmware Update 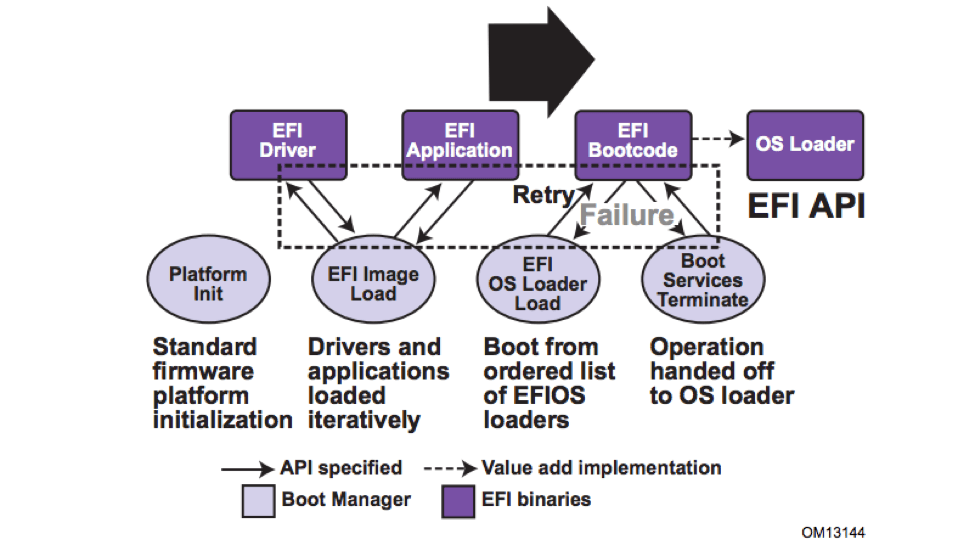
Turn off vulnerabilities in connected embedded devices
Capture the news headlines with a positive image