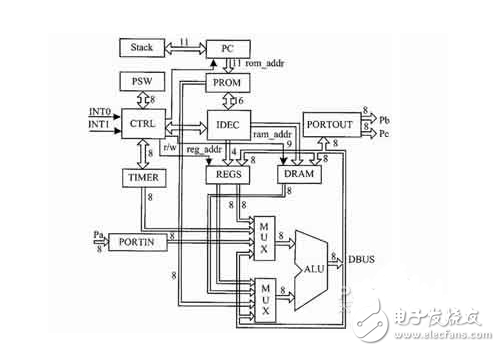
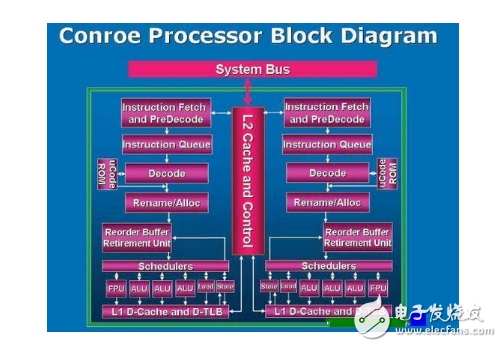
RISC is the abbreviation of "Reduced InstrucTIon Set CompuTIng" in English, meaning "reduced instruction set" in Chinese. It is developed on the basis of the CISC command system. Some people have tested the CISC machine and showed that the frequency of use of various instructions is quite different. The most commonly used instructions are simple instructions, which only account for 20% of the total number of instructions. However, the frequency of occurrence in the program is 80%. Complex instruction systems inevitably increase the complexity of the microprocessor, making the processor development time long and costly. And complex instructions require complex operations, which inevitably slow down the computer. Based on the above reasons, the RISC type CPU was born in the 1980s. Compared with the CISC type CPU, the RISC type CPU not only streamlined the instruction system, but also adopted a system called "superscalar and super-pipeline structure", which greatly increased the parallel processing capability. . The RISC instruction set is the development direction of high performance CPUs. It is opposed to the traditional CISC (complex instruction set). In contrast, RISC has a uniform instruction format, fewer types, and fewer addressing modes than complex instruction sets. Of course, the processing speed is much improved. At present, CPUs of this command system are widely used in medium and high-end servers, and in particular, high-end servers all use the CPU of the RISC command system. The RISC command system is more suitable for the high-end server operating system UNIX, and now Linux is also a UNIX-like operating system. RISC-type CPUs are not compatible with Intel and AMD CPUs in software and hardware. At present, the CPUs that use RISC instructions in medium and high-end servers mainly have the following types: PowerPC processors, SPARC processors, PA-RISC processors, MIPS processors, and Alpha processors. RISC's instruction set operations include HP's PA-RISC, IBM's PowerPC, Compaq (incorporated with HP) Alpha, MIPS' MIPS, and Sun's SPARC. Currently only UNIX, Linux, MacOS and other operating systems run on RISC processors. Common reduced instruction set microprocessors include AVR, PIC, ARM, DEC Alpha, PA-RISC, SPARC, MIPS, Power Architecture, and more. In the early days, this CPU instruction set was characterized by a small number of instructions, each instruction using a standard word length, a short execution time, and CPU implementation details visible to the machine level program. In fact, in the later development, RISC and CISC learn from each other in the process of quarreling. The current RISC instruction set has reached hundreds, and the operation cycle is no longer fixed. However, the fundamental principle of RISC design--for the pipeline Processor optimization - no change. The five clock cycles are: IF (InstrucTIon fetch), ID (InstrucTIon decode/register fetch cycle), EX (Execution/effective address cycle), MEM (Memory access), WB (Write-back cycle). IF: According to the memory address stored in the PC (program counter), the instruction pointed to by the address is found in the memory, and the instruction is stored in the register. At the same time, the PC points to the next instruction. To complete this operation, the PC is required to add 4 (take the 32-bit instruction set as an example, if it is 64-bit, add 8). ID : The instruction obtained from the IF stage. Decode the instruction and finally find the data stored in the registers needed by the instruction. If the instruction has only one jump instruction, then at this stage, the obtained value needs to be compared according to the meaning of the jump instruction. If the comparison result is true, the jump is performed. If the comparison result is false, the jump is not executed, and the continuation is continued. Execution of the next instruction; if the instruction needs to fill some bits in the instruction, it is also done in the ID phase, such as filling the upper four bits to satisfy the instruction result is 32 bits; calculating the address of the instruction that may jump. EX : ALU (Arithmetic Logic Unit) calculates the result of the ID phase. In the ID stage, the values ​​of the registers required for the instruction calculation have been obtained, so in the EX stage, the values ​​of these registers need to be calculated according to the meaning of the instructions. The calculation becomes different depending on the instruction. There are three main types of ALU calculations: 1. The ALU calculates the valid address unit based on the address supplemented in the ID, and finally obtains the address of the required memory; 2. According to the meaning of the instruction, the value obtained from the register, To perform operations, such as adding the values ​​of two registers; 3. Calculating the result of the immediate value based on the value of the register and the supplemental value. MEM: If the current instruction is a Load instruction, then according to the memory address calculated by EX, the corresponding value is obtained from the memory; if the current instruction is store, then the memory address and the value of the register calculated according to EX, the register The value is stored in this memory address. Other instructions generally do not design memory access. WB: Write the calculated value of the final register to the register file. This operation includes values ​​obtained from memory and results obtained by arithmetic operations. The above five clock cycles are the main steps in the execution of a RISC instruction. There are few types of instructions, instruction format specifications: The RISC instruction set usually uses only one or a few formats. The instruction length is single (typically 4 bytes) and aligned on word boundaries, and the position of the field, especially the opcode, is fixed. Simplified addressing: Almost all instructions use register addressing, and the total number of addressing modes is generally no more than five. Other more complex addressing methods, such as indirect addressing, are synthesized by software using simple addressing methods. Extensive use of inter-register operations: Most operations in the RISC instruction set are register-to-register operations that access memory only with simple Load and Store operations. Therefore, there is no more than one memory address accessed per instruction, and access to memory is not mixed with arithmetic operations. Simplified processor architecture: Using the RISC instruction set greatly simplifies the design of the processor's controllers and other functional units without having to use a large number of dedicated registers, especially allowing hardware-lined instruction operations without having to use them like CISC processors. Microprograms to implement instruction operations. Therefore, the RISC processor does not have to set up the microprogram control memory like the CISC processor, and can execute the instructions directly and quickly. Easy to use VLSI technology: With the development of LSI and VLSI technology, the entire processor (or even multiple processors) can be placed on one chip. The RISC architecture can bring many benefits to designing a single-chip processor, which can improve performance and simplify the design and implementation of VLSI chips. Based on VLSI technology, manufacturing RISC processors is much less expensive and much less expensive than CISC processors. Enhanced processor parallelism: The RISC instruction set is very efficient for pipeline, superpipeline, and superscalar techniques for instruction-level parallelism and improved processor performance. At present, the commonly used processor internal parallel operation technology is basically based on the development and maturity of the RISC architecture. Universal Back Sticker, Back Film, TPU Back Sticker, Back Skin Sticker, PVC Back Sticker, Back Skin,Custom Phone Sticke,Custom Phone Skin,Phone Back Sticker Shenzhen Jianjiantong Technology Co., Ltd. , https://www.jjtscreenprotector.com