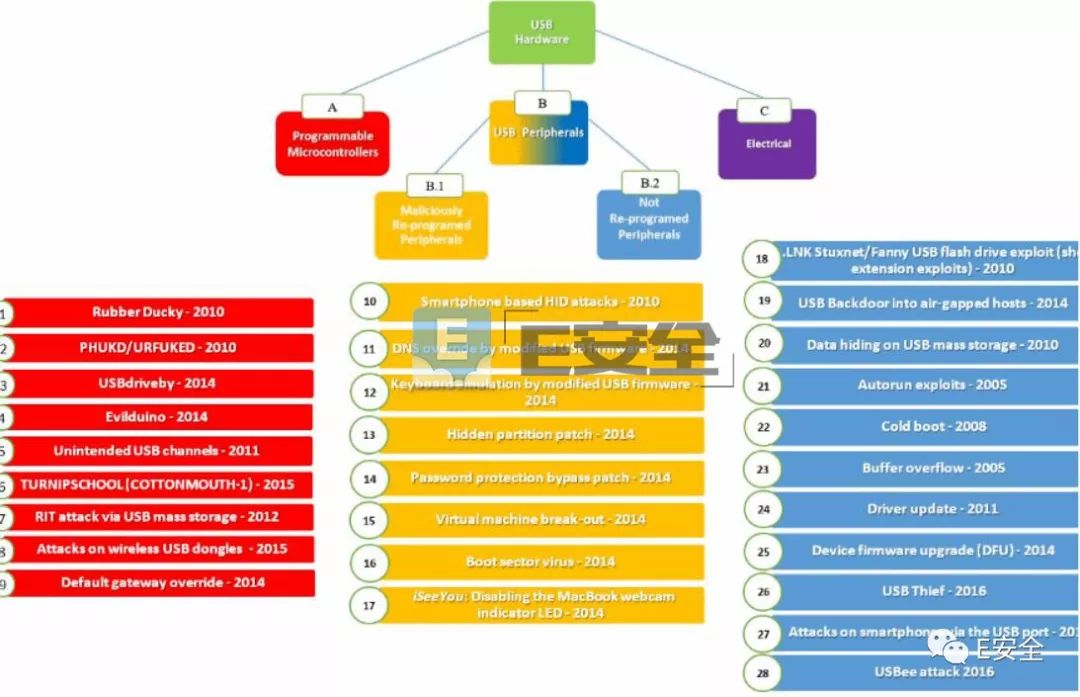
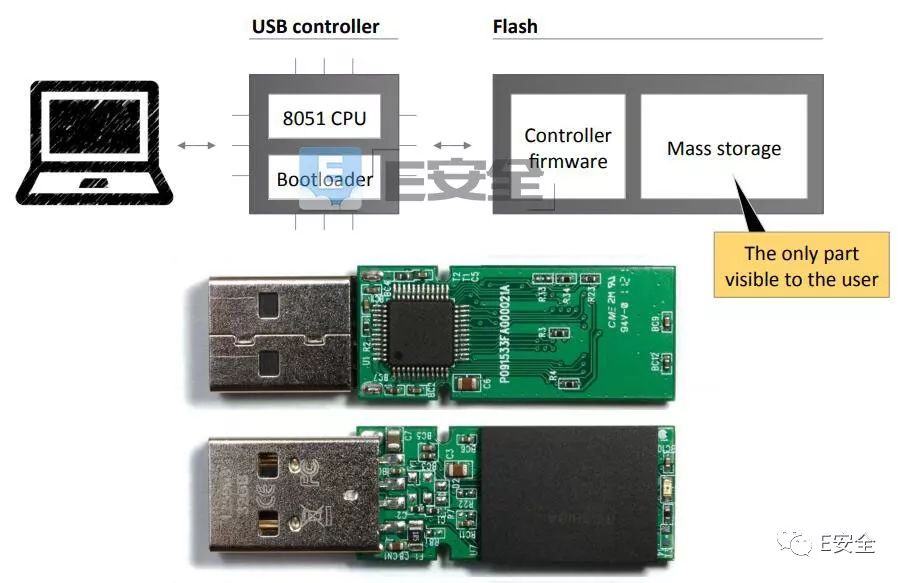
1. Reprogram the internal microcontroller of the USB device. Such a device appears to be no different from a normal USB device (such as a charger), but it is quietly performing other operations, such as injecting a keyboard tap; Second, by reprogramming the USB device firmware to perform malicious operations, such as malware downloads, data leakage, etc. Third, there is no need to reprogram the USB device firmware, but use the security flaws in the operating system to interact with the USB protocol/standard; Fourth, USB-based electronic attacks. First, USB attack reprogramming the internal microcontroller 1) Rubber Ducky: A commercial keyboard tapping injection attack platform, released in 2010. Once connected to the host computer, the Rubber Ducky is recognized as a keyboard and injected into the sequence of keystrokes that are preloaded. 2) PHUKD/URFUKED attack platforms: Similar to Rubber Ducky, but allows an attacker to choose when to inject a malicious keyboard tap. 3) USBdriveby: emulates a USB keyboard and mouse, and silently installs and overwrites the DNS settings on the unlocked OS X host via USB in a few seconds. 4) Evilduino: Similar to PHUKD/URFUKED, but using Arduino microcontroller instead of Teensy. The keyboard/mouse is also simulated and a keyboard tap/mouse pointer move operation can be sent to the host based on a preloaded script. 5) Unintended USB channel: A proof of concept (POC) USB hardware Trojan that uses an unexpected USB channel (such as a USB speaker) for data leakage. 6) TURNIPSCHOOL (COTTONMOUTH-1): Hardware implant hidden in the USB cable. Developed by the National Security Agency (NSA). 7) RIT attack via USB mass storage device: It will tamper with the contents of the file when the USB mass storage device is connected to the victim computer. 8) Attacks on wireless USB dongles: Attacks on Wireless USB dongle - A type of attack that occurs after Samy Kamkar releases the KeySweeper attack platform. This tool can secretly record and decrypt the input of multiple Microsoft RF wireless keyboards. 9) Default Gateway Override: This attack uses a microcontroller to trick the USB Ethernet adapter to override DHCP settings and hijack local traffic. Second, maliciously modify the attack of USB firmware 10) Smartphone-based HID attacks: First appeared in a research paper, the researchers created a variety of customized Android accessory drivers that can override legitimate drivers when Android interacts with USB devices. The malicious driver emulates the USB keyboard and mouse connected to the phone by interacting with the Android USB accessory API. 11) Modify the USB firmware to overwrite the DNS: The researchers modified the firmware of the USB stick and used it to emulate the USB Ethernet adapter and then used it to hijack local traffic. 12) Simulate the keyboard by tampering with the USB firmware: Several researchers showed how to infect the U disk firmware and use this to inject keyboard taps. 13) Hidden Partition Patch: The researchers showed how to reprogram a USB flash drive to create a hidden partition that could not be formatted for data leakage. 14) Password Protection Bypass Patch: Minor changes to the U disk firmware, allowing an attacker to bypass a password-protected USB drive. 15) Virtual Machine Break-Out: Researchers use USB firmware to invade the virtual machine environment. 16) Boot Sector Virus: Researchers use a USB flash drive to infect a computer before it boots. 17) iSeeYou: A proof-of-concept project that reprograms a class of Apple's built-in iSight camera to secretly record video without triggering the LEF indicator. Third, no reprogramming USB device attack 18) CVE-2010-2568. LNK security exploits exploited by Stuxnet and Fanny malware. 19) USB backdoor for intrusion into the host: Map the computer to the wireless network using Fanny malware (developed by the US National Security Agency's equation team) via the USB hidden storage save preset command. The information on the network will be saved to the hidden storage space of the USB flash drive. 20) Hide data in USB mass storage devices: Collect a large amount of hidden malware or stolen data in the USB drive (for example, store data outside the normal partition, or hide it by making the folder icon and name transparent) Documents, etc.). 21) AutoRun Exploits: Depending on the configuration of the host computer, some PCs will automatically execute certain files in the USB device storage space. This type of malware is specifically named autorun malware. 22) Cold Boot Attacks: RAM dump attacks. The attacker can store the contents of the memory in the U disk and leak RAM data by booting with a USB device. 23) Buffer Overflow Based Attacks: When a USB device is plugged into a computer, some of the attacks can exploit the buffer overflow vulnerability in the operating system. This is the case because the operating system enumerates devices and functions (running certain scheduled operations) when accessing a USB device. 24) Driver Update: A very sophisticated attack that relies on the acquired VeriSign Class 3 organization certificate and submits the driver to Microsoft. When a USB device is plugged in, the user PC will automatically install it. Although this kind of attack has theoretical feasibility, it is difficult to actually use it in reality. 25) Device Firmware Upgrade (DFU for short): An attacker can use the Device Firmware Upgrade (DFU), a legitimate process supported by the USB standard, to update local legitimate firmware to a malicious version. 26) USB Thief: A U disk drive-based data theft malware recently discovered by ESET. 27) Attacking a smartphone via the USB interface: An attacker can hide and deliver malware through a USB phone charger. 28) USBee attack: Use the data bus of the USB connector to emit electromagnetic radiation that can be used for data leakage. Fourth, power attack 29) USB Killer: Permanent damage to the device by inserting a USB device to trigger a current overload. The research team at Ben Gurion University published an article in ScienceDirect magazine in 2017, which details all of the above attacks. The purpose of this study is to alert users that various USB devices are likely to be used to infect their systems while secretly stealing data from protected and wireless networks in a variety of ways. The research team recommends disabling USB devices in a secure network, or at least strictly controlling them.
Ethernet cables connect devices such as PCs, routers, and switches within a local area network.Most technicians refer to these standards as CAT5 and CAT6, respectively. Also CAT3 available. Because of this, many online stores that sell network cables use this abbreviated language as well.
The connector can by shield or non-shield type, raw cable can be UTP, STP, FTP type. Also the molded shape can be custom mould by straight, right-angle, 105 degree, etc.
These physical cables are limited by length and durability. If a network cable is too long or of poor quality, it won't carry a good network signal. These limits are one reason there are different types of Ethernet cables that are optimized to perform certain tasks in specific situations.
Ethernet Cable Wiring,RJ45 cable,networking cable,8P8C cable ETOP WIREHARNESS LIMITED , https://www.oemmoldedcables.com
On March 28th, Israeli researchers studied 29 ways to use USB devices to invade users' computers and classify them into the following four categories: